Features That Make a Difference
Why Choose Centraleyezer?
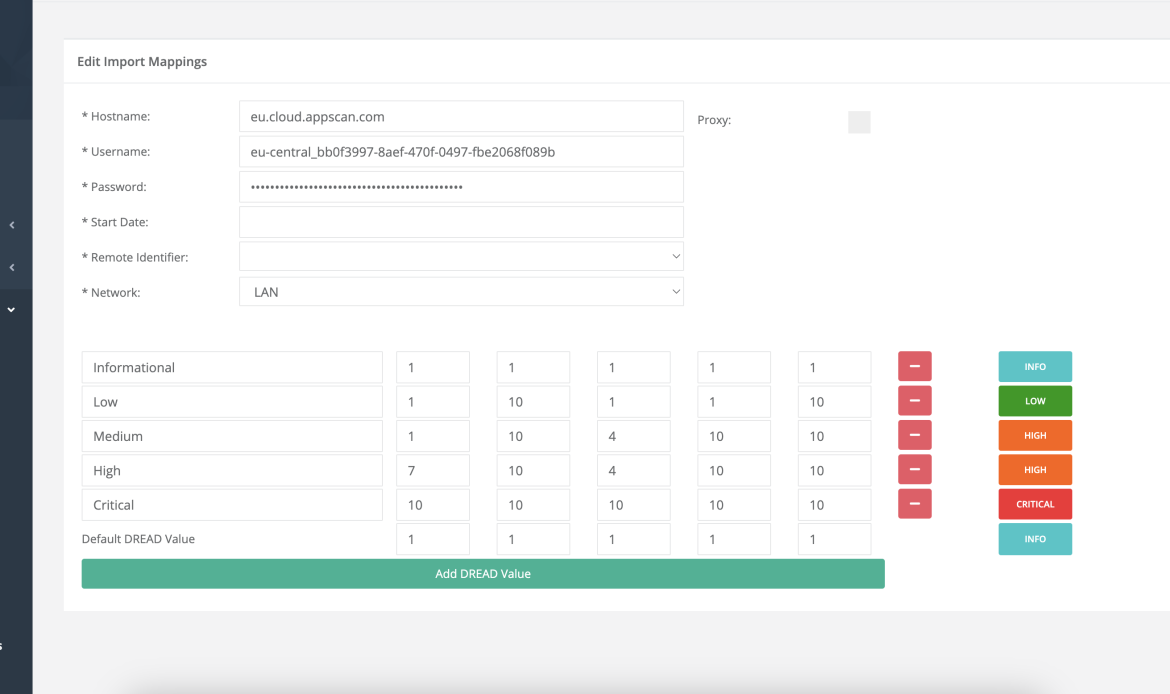
Vulnerability Tracking
Consolidate VA Scans
Vulnerability Escalation
Enterprise Ready
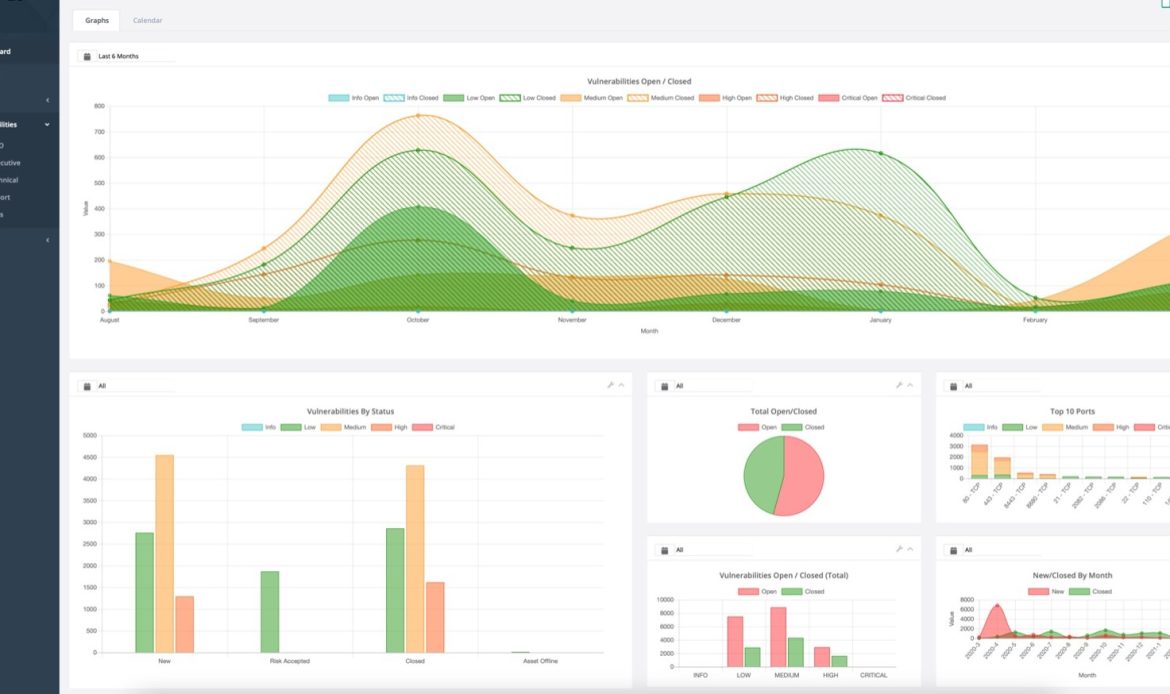
Security Dashboard
Automatic Notifications
User Permissions
It allows tracking of manual penetration tests vulnerabilities into an unified view.
Consolidates and aggregates Dynamic (DAST) vulnerability scans.
Automates Vulnerability escalation process to responsible persons.
Single Sign-On Active Directory.
Unique security state view for each user based on assigned rights.
Automatic Follow-up on vulnerabilities. Automatic Escalation after reaction time deadline expires
Granular user permissions based on roles and asset permissions.
It's all about to be pro!
Pricing
Start Your Free Trial Today!
Don't wait for a security breach—take proactive steps now.




