Trustwave Summary
The integration of Trustwave security solutions with the Centraleyezer Vulnerability Management platform enhances the import and management of security findings. This collaboration enables organizations to efficiently identify, prioritize, track, and remediate vulnerabilities, improving their overall security posture and risk management.
Trustwave Key Features
Data Import:
- Import assets, scan summaries, and vulnerabilities from Trustwave security tools into Centraleyezer, either on-demand or via automated schedules.
- Supported formats: CSV.
Detailed Findings:
- Centraleyezer provides comprehensive vulnerability details based on Trustwave security assessments.
Risk Scoring:
- Configurable severity values for Trustwave findings, aligned with organizational risk policies.
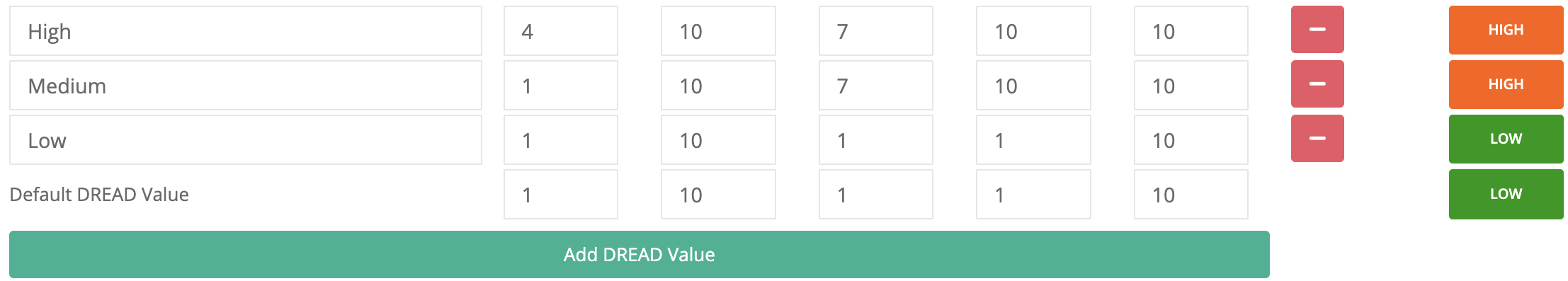
Selective Data Import:
- Supports filtering based on status, scan type, and severity for more precise data imports.
Considerations
- The integration supports mapping one Trustwave instance with one Centraleyezer instance.
- Configuring a different Trustwave instance in the plugin will overwrite previously imported data.
Requirements
System Requirements:
- Centraleyezer Prerequisites: Latest version of the Centraleyezer Vulnerability Management Platform is recommended.
- Trustwave Prerequisites: API access must be enabled with proper authentication and must support findings export and API-based integration.
Permissions and Roles:
- Centraleyezer: Requires System Admin or Application Security Manager permissions.
- Trustwave: User access for vulnerability scan results.
- Import mappings require admin-level permissions.
Release Notes
Version 1.0.0:
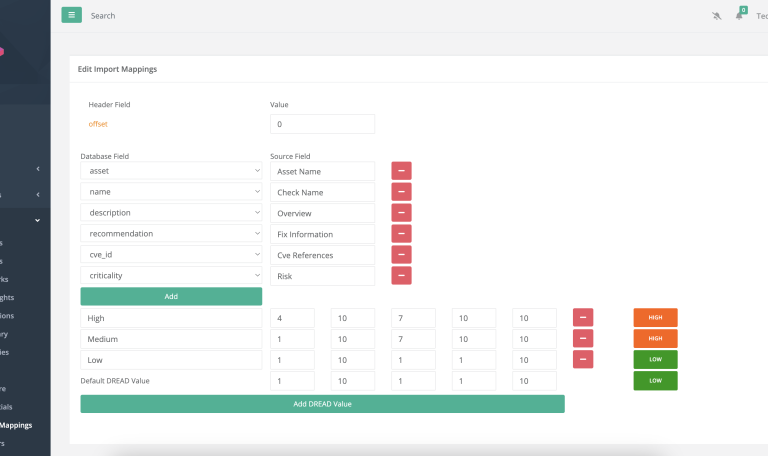
Mapped vulnerabilities from Trustwave security scans, including:
- Asset
- Name
- Description
- Recommendation
- CVE ID
- Criticality