Summary
HCL AppScan Cloud (DAST findings) can be integrated with the Centraleyezer Vulnerability Management platform to streamline the import of vulnerability data. This integration helps businesses efficiently identify, prioritize, track, and remediate security vulnerabilities.
Key Features
Data Import:
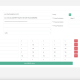
Import applications, scan summaries, and application-vulnerable items into your Centraleyezer instance either on-demand or based on pre-configured automated schedules.
Detailed Findings:
Complete request/response information for DAST vulnerabilities is provided by Centraleyezer.
Risk Scoring:
Configurable severity value for HCL AppScan Cloud (DAST findings) assessments, which can be adjusted based on organizational risk policies.
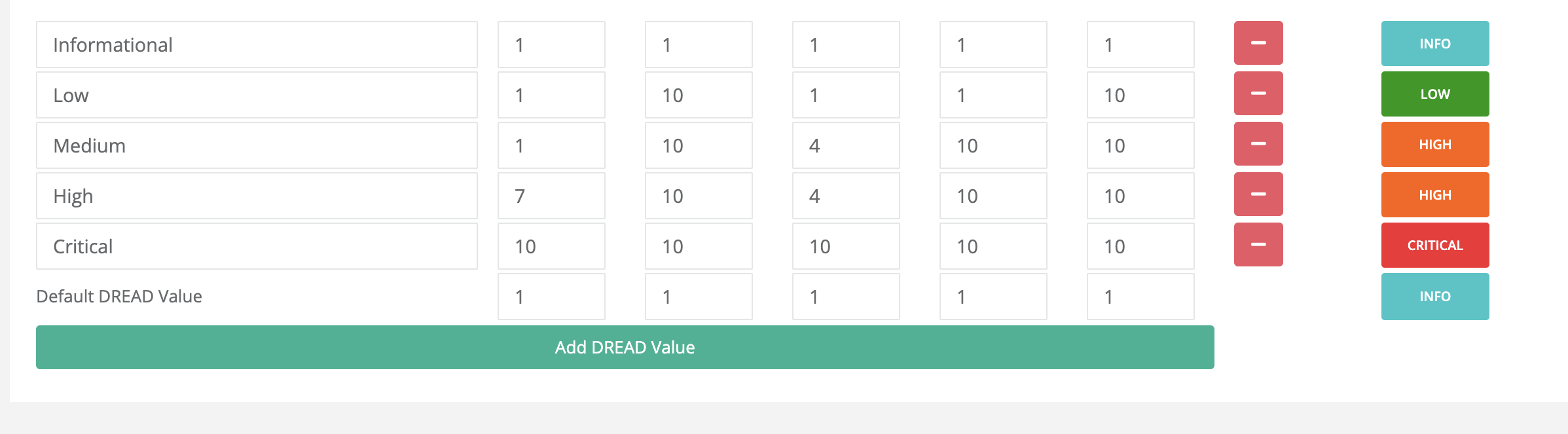
Selective Data Import:
Supports configuration filters based on status, scan type, and severity for selective data import.
Must-Have Connection:
An HTTPS connection is required, with or without a proxy.
Considerations
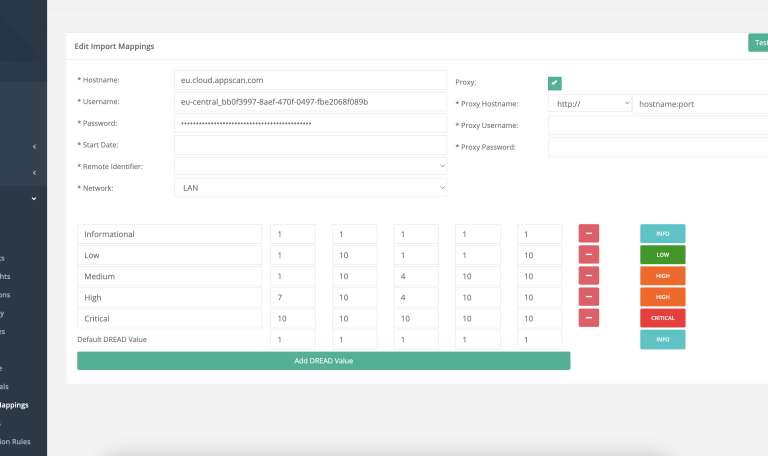
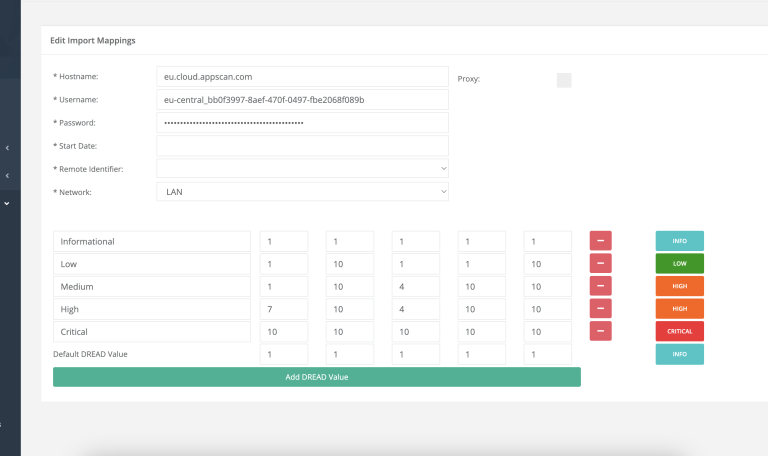
The plugin supports mapping one HCL AppScan Cloud Server with one Centraleyezer instance. Configuring a different AppScan Cloud Server in the plugin will overwrite previously imported data.
Requirements
System Requirements
Centraleyezer Prerequisites:
Latest version of the Centraleyezer Vulnerability Management Platform is recommended.
AppScan Cloud Prerequisites:
HCL AppScan Cloud API access.
Permissions and Roles
System Admin (admin) or Application Security Manager (part of App-Sec Manager group) permissions required.
HCL AppScan Cloud user access for DAST scan information.
Permissions must be assigned to “admin” for import mappings.
Release Notes
Version 1.0.0
Mapped vulnerabilities from HCL AppScan during DAST scans with the following fields:
Name: IssueType
CVE: Cve
CVSS: Cvss
CWE: Cwe
Asset: Constructed from scheme, domain, and path.
Severity: Severity
CVSS3 Score: cvss3_score
Protocol: protocol (defaults to ‘N/A’ if not specified)
Port: Port (defaults to 0 if not specified)
Targets: Includes location, element type, and element details.
Import Vulnerability ID: IssueTypeId
Permissions: Required to access import mappings.
Summary
HCL AppScan Cloud (SAST findings) can be integrated with the Centraleyezer Vulnerability Management platform to streamline the import of vulnerability data. This integration helps businesses efficiently identify, prioritize, track, and remediate security vulnerabilities.
Key Features
Data Import:
Import applications, scan summaries, and application-vulnerable items into your Centraleyezer instance either on-demand or based on pre-configured automated schedules.
Detailed Findings:
Complete request/response information for SAST vulnerabilities is provided as an attachment by Centraleyezer.
Risk Scoring:
Configurable severity value for HCL AppScan Cloud (SAST findings) assessments, which can be adjusted based on organizational risk policies.
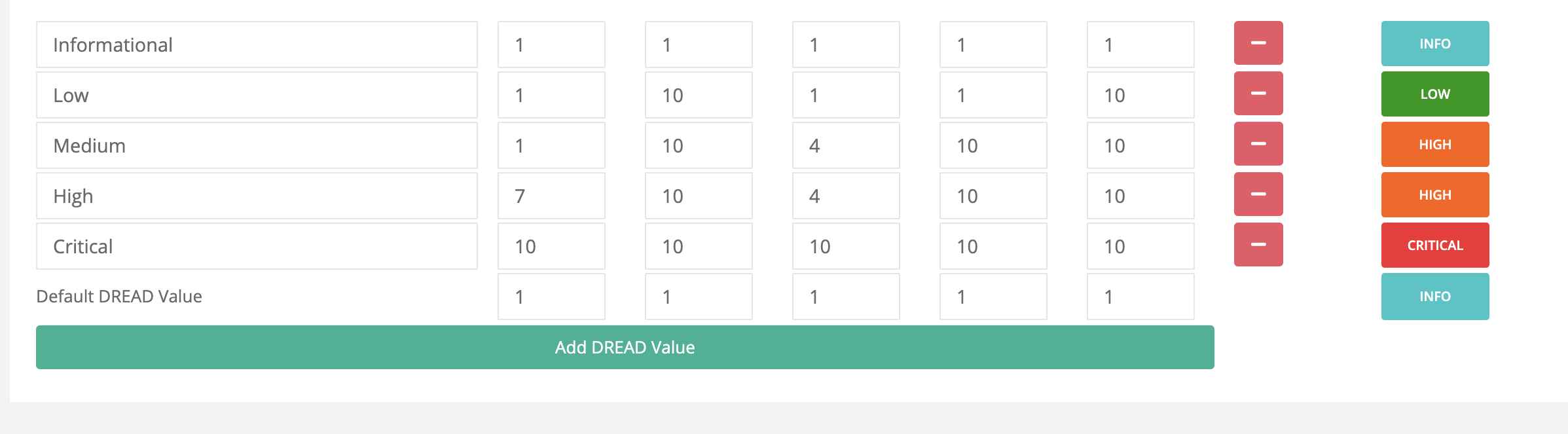
Selective Data Import:
Supports configuration filters based on status, scan type, and severity for selective data import.
Must-Have Connection:
An HTTPS connection is required, with or without a proxy.
Considerations
The plugin supports mapping one HCL AppScan Cloud Server with one Centraleyezer instance. Configuring a different AppScan Cloud Server in the plugin will overwrite previously imported data.
Requirements
System Requirements
Centraleyezer Prerequisites:
Latest version of the Centraleyezer Vulnerability Management Platform is recommended.
AppScan Cloud Prerequisites:
HCL AppScan Cloud API access.
Permissions and Roles
System Admin (admin) or Application Security Manager (part of App-Sec Manager group) permissions required.
HCL AppScan Cloud user access for SAST scan information.
Permissions must be assigned to “admin” for import mappings.
Release Notes
Version 1.0.0
Mapped vulnerabilities from HCL AppScan during SAST scans with the following fields:
Name: IssueType
CVE: Cve
CVSS: Cvss
CWE: Cwe
Asset: Constructed from scheme, domain, and path.
Severity: Severity
CVSS3 Score: cvss3_score
Protocol: protocol (defaults to ‘N/A’ if not specified)
Port: Port (defaults to 0 if not specified)
Targets: Includes location, element type, and element details.
Import Vulnerability ID: IssueTypeId
Permissions: Required to access import mappings.